-
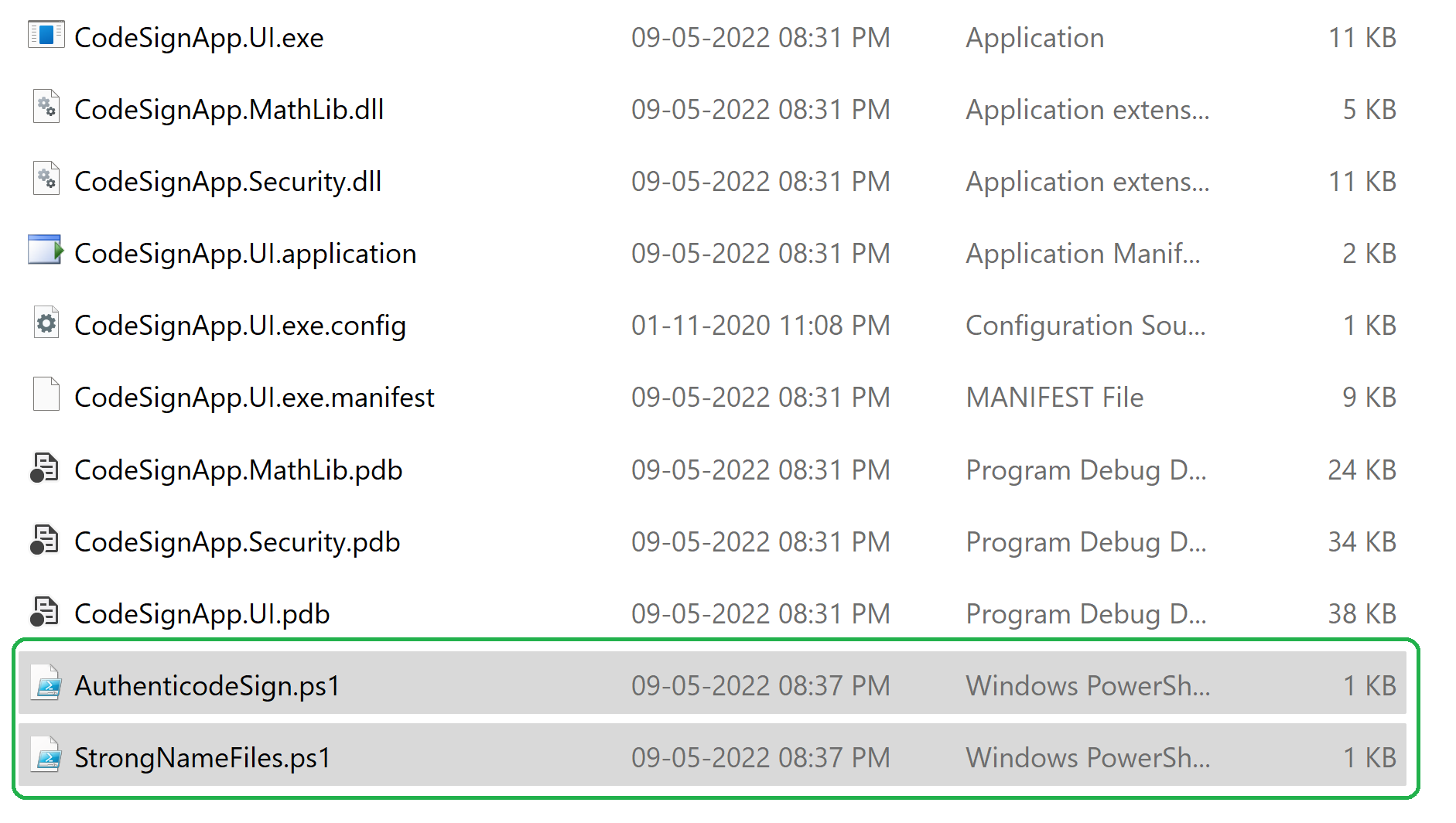
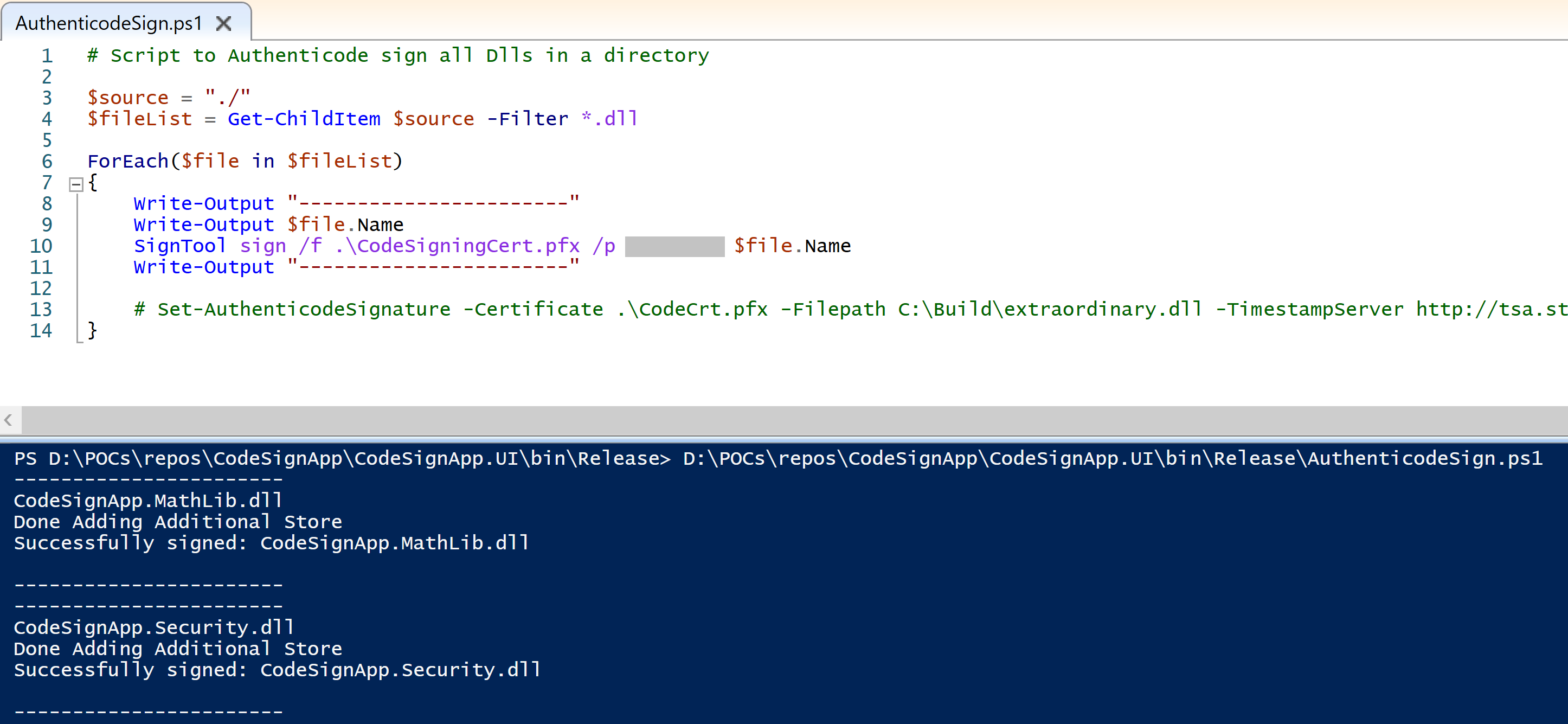
Adding two scripts to sign all DLLs
Copied two Powershell scripts into the build output folder. These are nothing but a very small script iterate signing process over all exe/dll in the present folder.
-
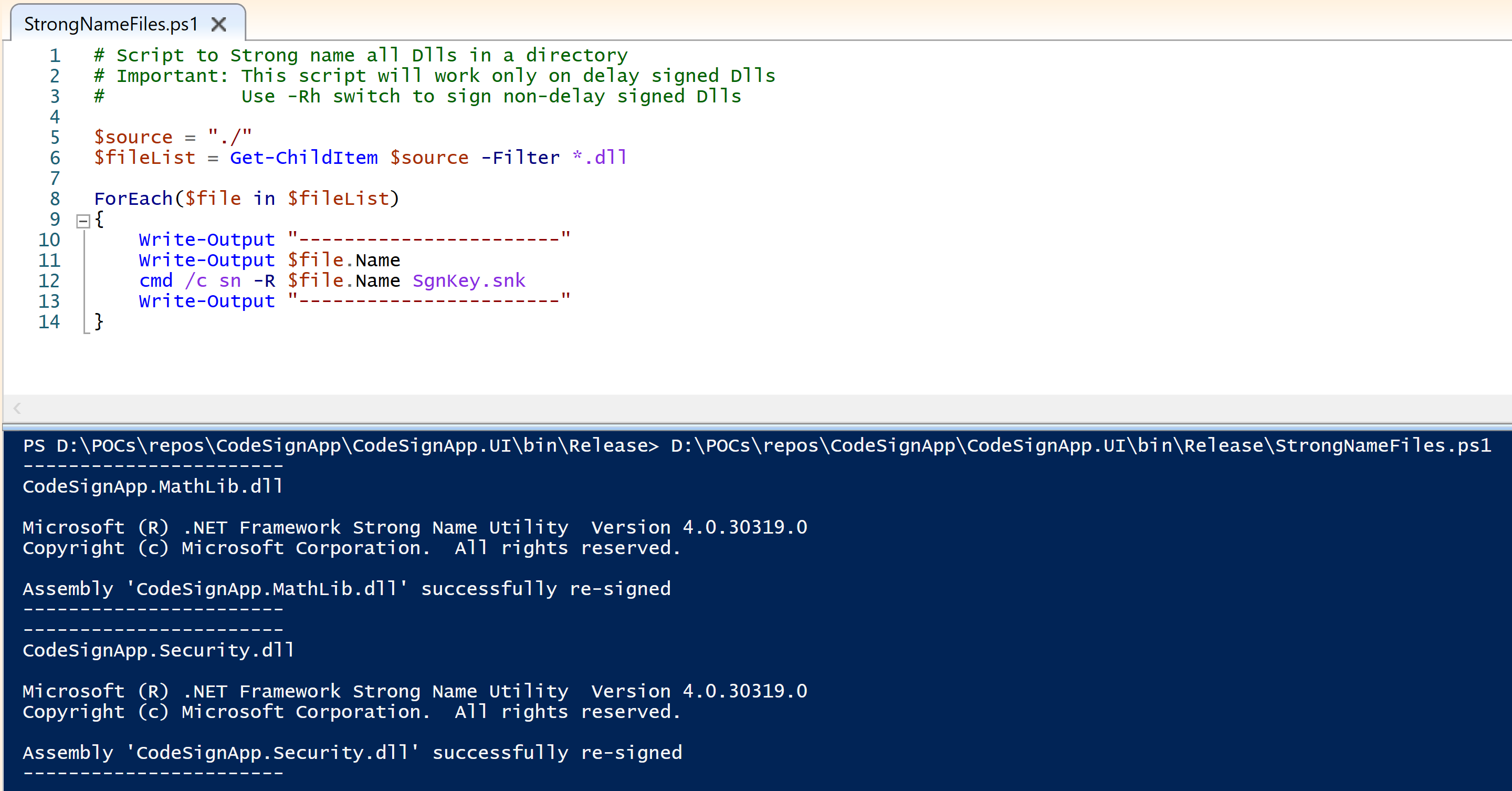
Add StrongName signing
Strong name the delay signed DLL using Signing key.
-
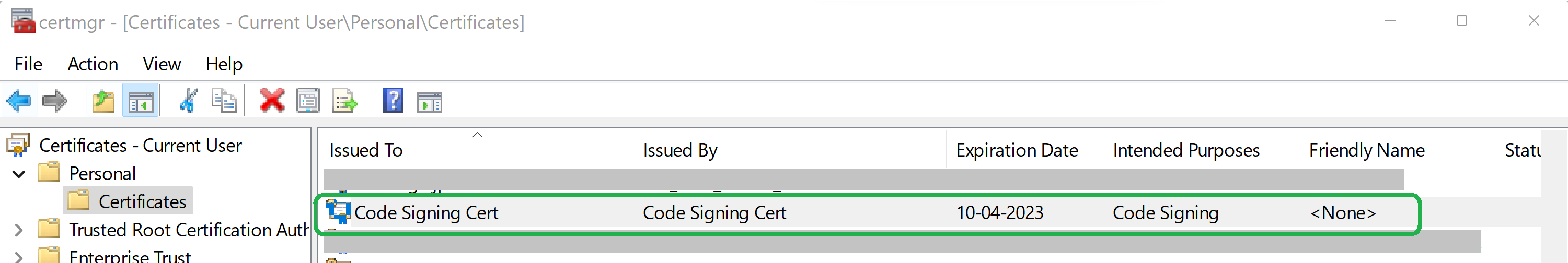
Create Authenticode signing certificate
Create Code signing cert to Cert store

-
Export the PFX file
Export the PFX file and provide a password when prompted during export process.
(Note: We can export it using PowerShell command also, Export-PfxCertificate -Cert "Cert:\CurrentUser\My\$($cert.Thumbprint)" "d:\CodeSigningCert.pfx" -Password
) 

-
Add Authenticode sign
We can sign and verify signing using below commands:
signtool sign /f .\CodeSignCert.pfx /p
.\MyAssembly_signed.dll 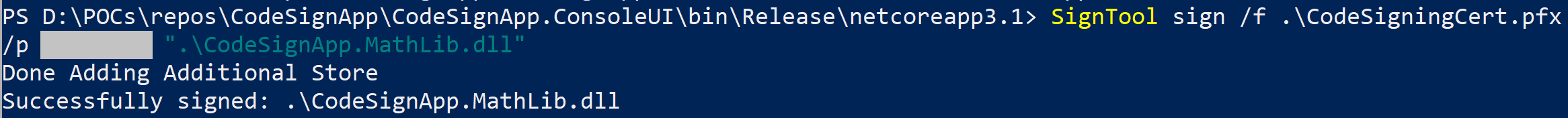
-
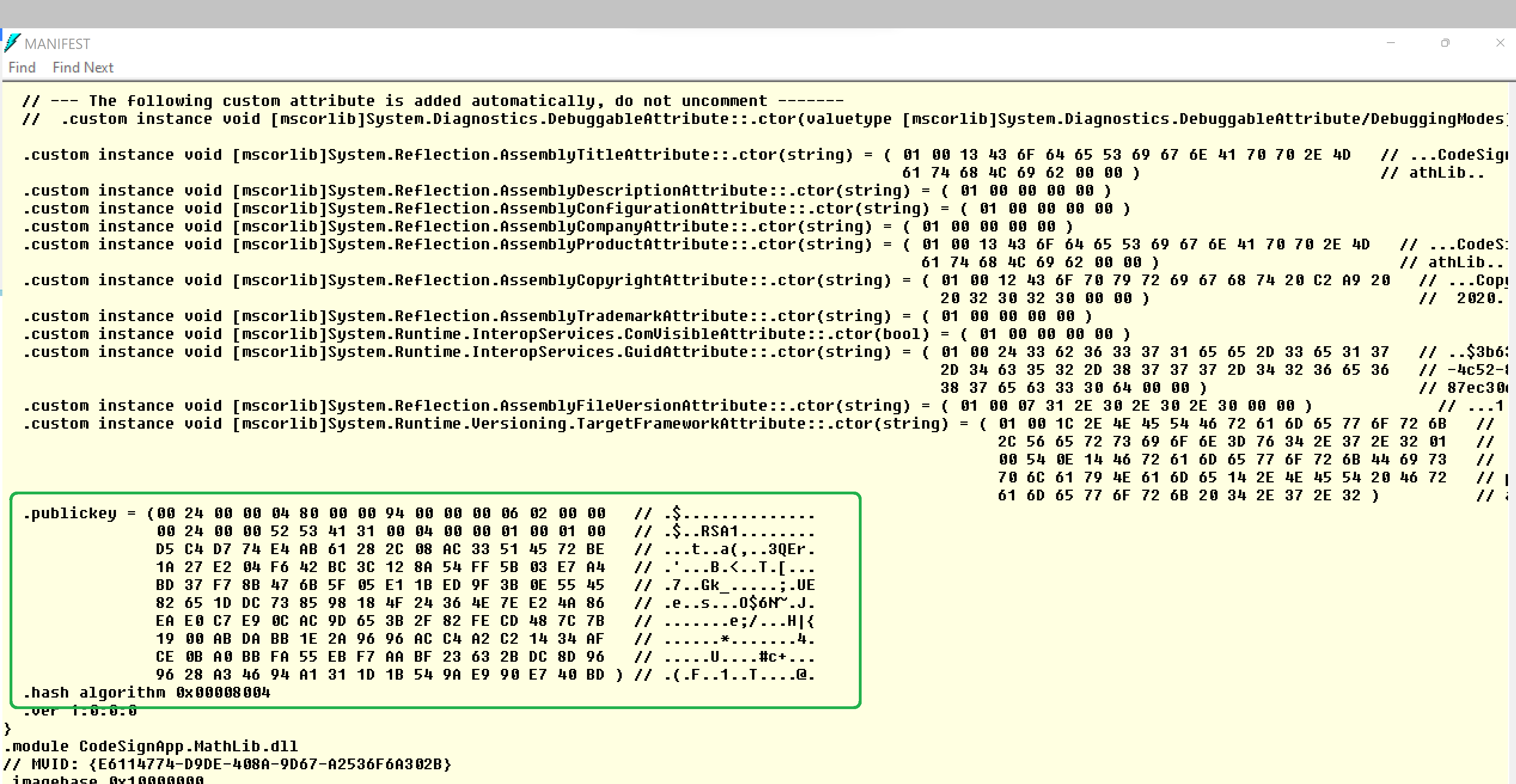
Check DLL metadata again
Now we can see that a new block has been added. This is the public key added for strong naming.
(Note: Delay signing also adds the public key details to the manifest. It is basically the public key value in "public.snk" file)
-
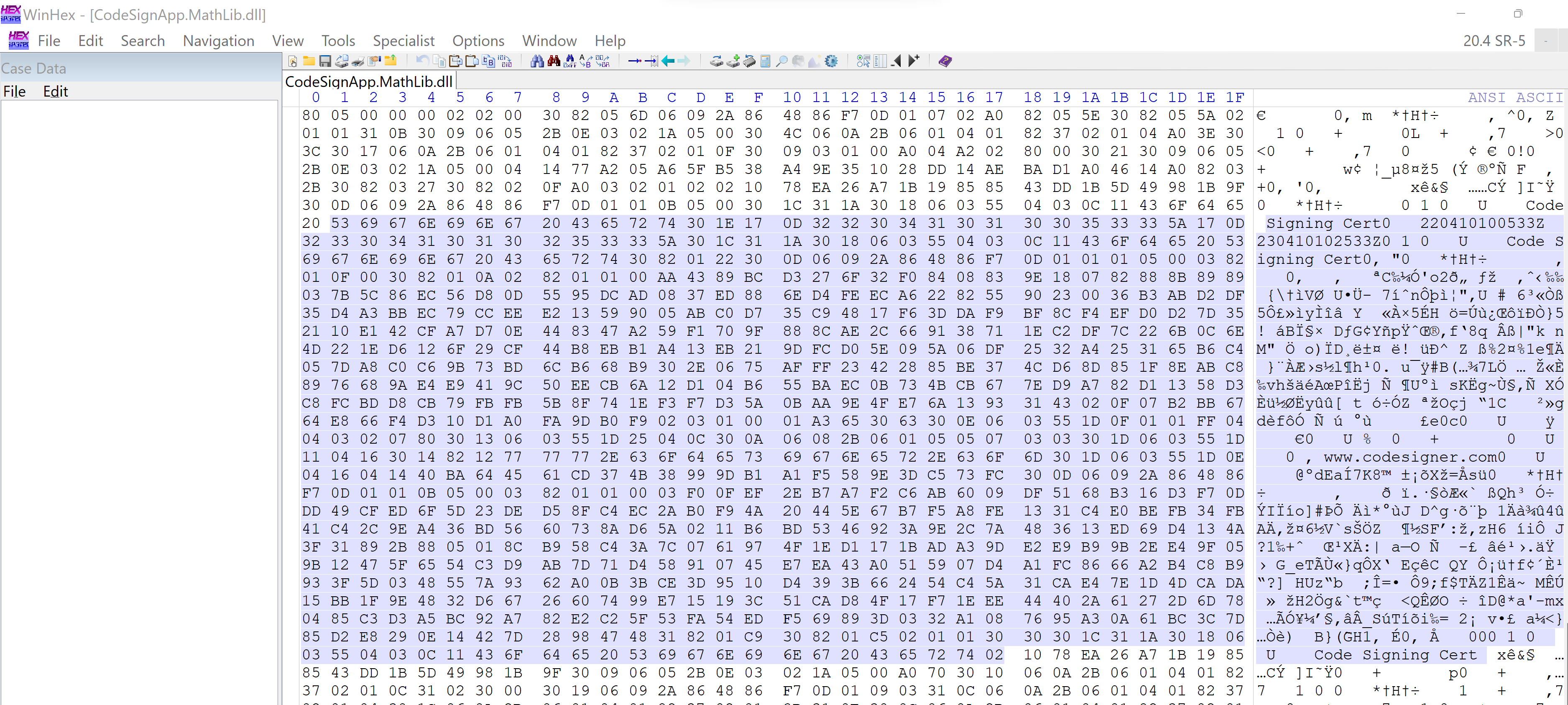
Check PE content
Authenticode signature data can also find from the file content.
-
Add Code sign certificate to Trusted Root store
The signature validation is being passed on this machine as the code signing cert has been added to the Trusted Root store in this machine. Otherwise, program won't start up and if we check the inner exception, it will say root certificate is not trusted.
-
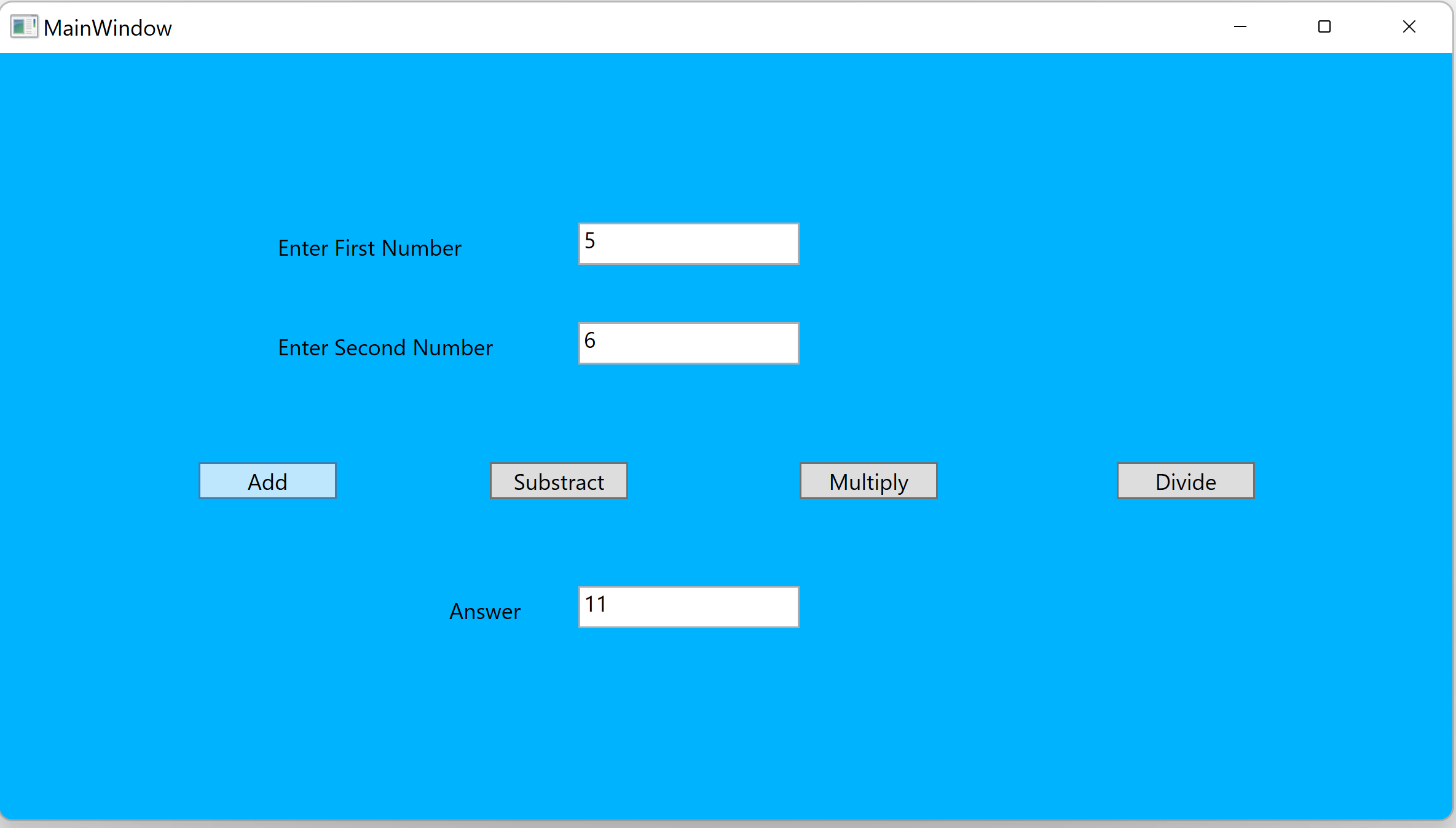
Run the application
Now, if we run the Exe again from the Release folder, the Calculator App will start.