We have seen how to add StrongName & Authenticode sigining for Windows executables and validations of same in Part-1.
This part will cover modifying DLL and whether StrongName or Authenticode signing helps to ensure integrity(anti-tampering) and authenticity of software executable files. The scenario here can considered as a software supply chain where the Calculator DLL(CodeSignApp.MathLib.dll) library is obtained from a trusted third party and the Entry app need to validate the integrity and authenticity of the library before using it in the application.
Malicious agent can try to modify the DLL library and can sign it with his own StrongName/Authenticode signing keys and supply it to the production environment.
Code for the same can be found here : https://github.com/violet-devsec/wpf-app-dll-code-sign
-
Create another strong name keypair.
We consider it as attacker's StrongName key.
-
Create another Authenticode signing certificate.
We consider it as attacker's Authenticode certificate.
-
Export the new certificate to machine folder.

-
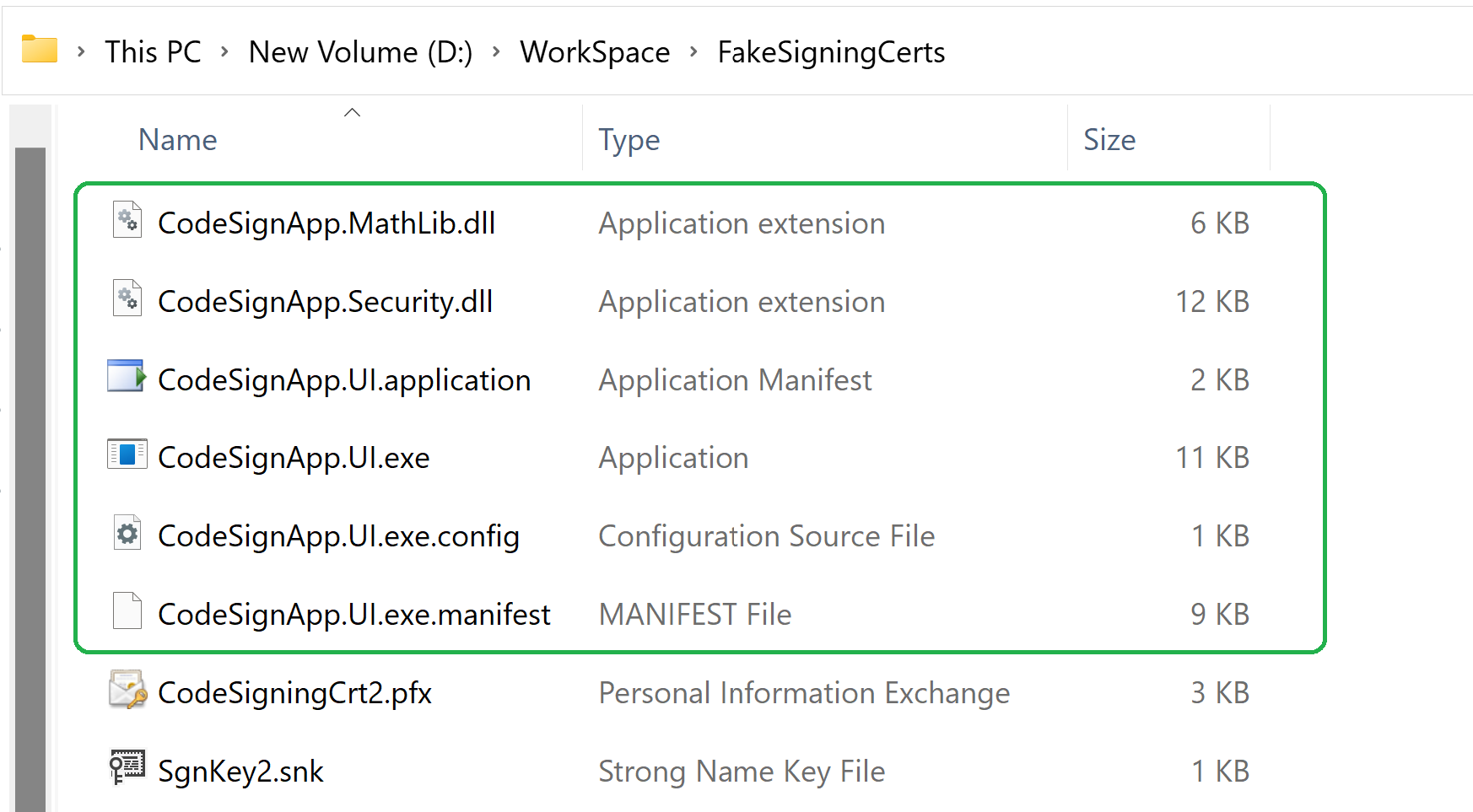
Move the Exe and Dll files to a new folder
This is just to do our modification process on a copy of original executables.
-
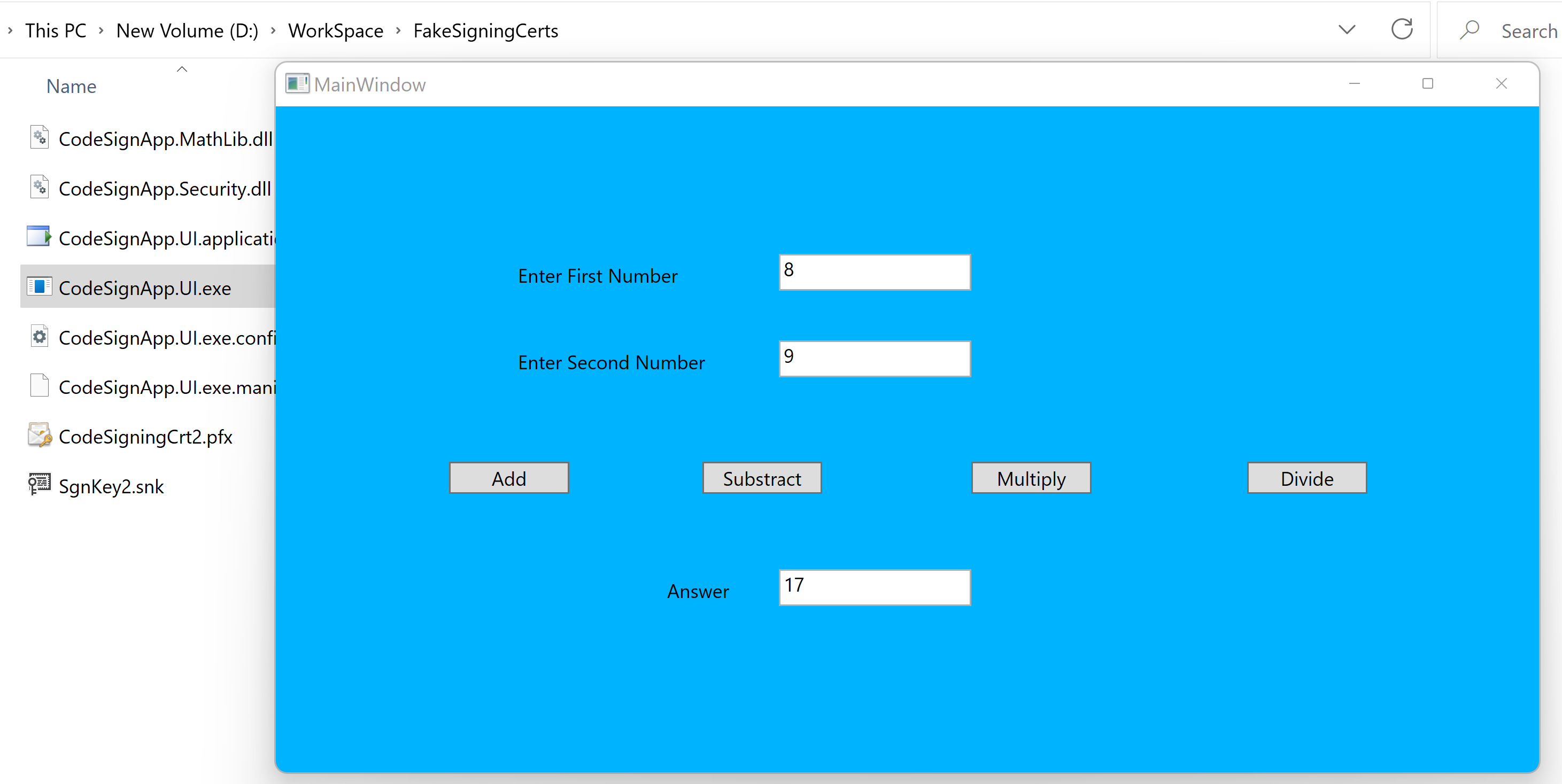
Run the application
Just to verify the normal execution of the application.
-
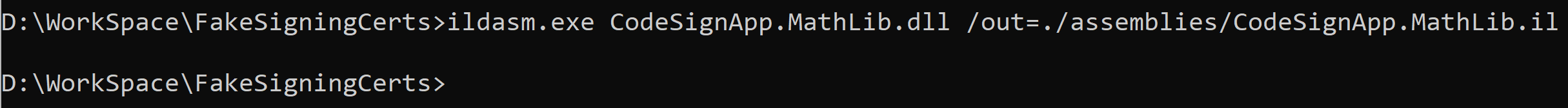
Disassemble the DLL
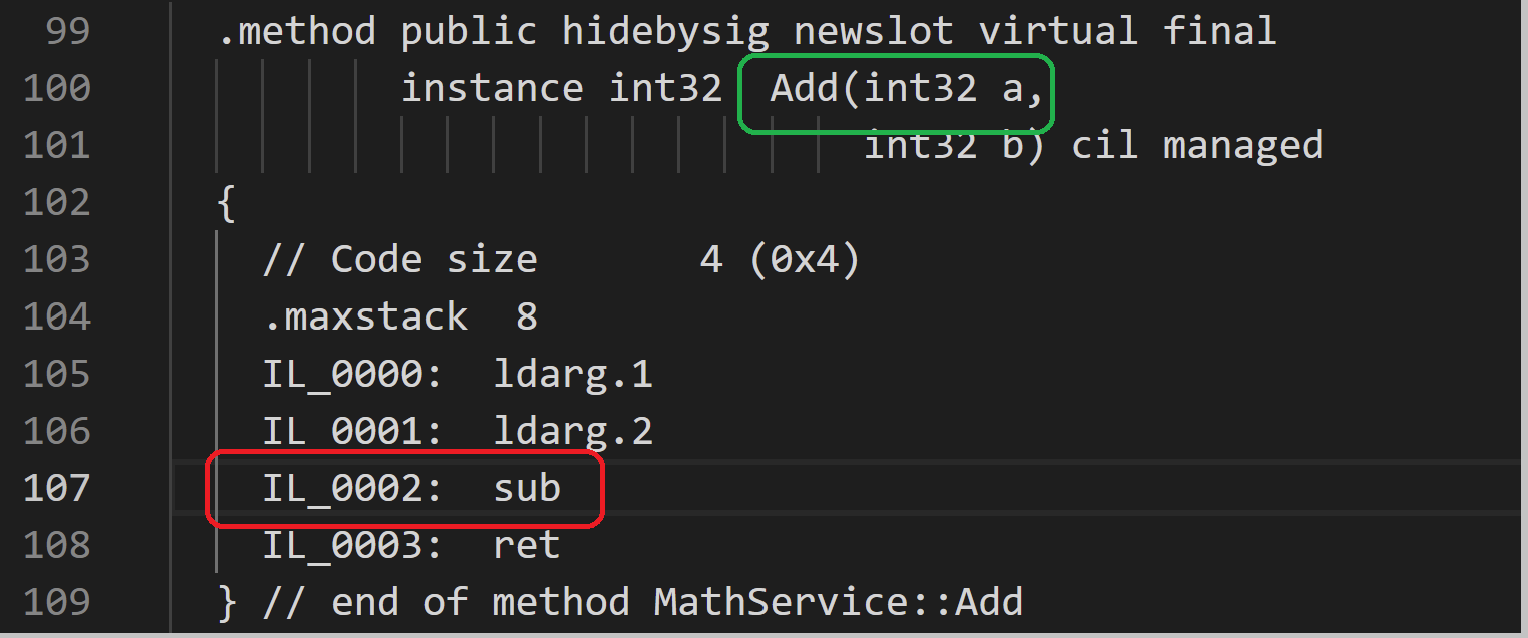
Now we are going to modify the "CodeSignApp.MathLib.dll" file.
-
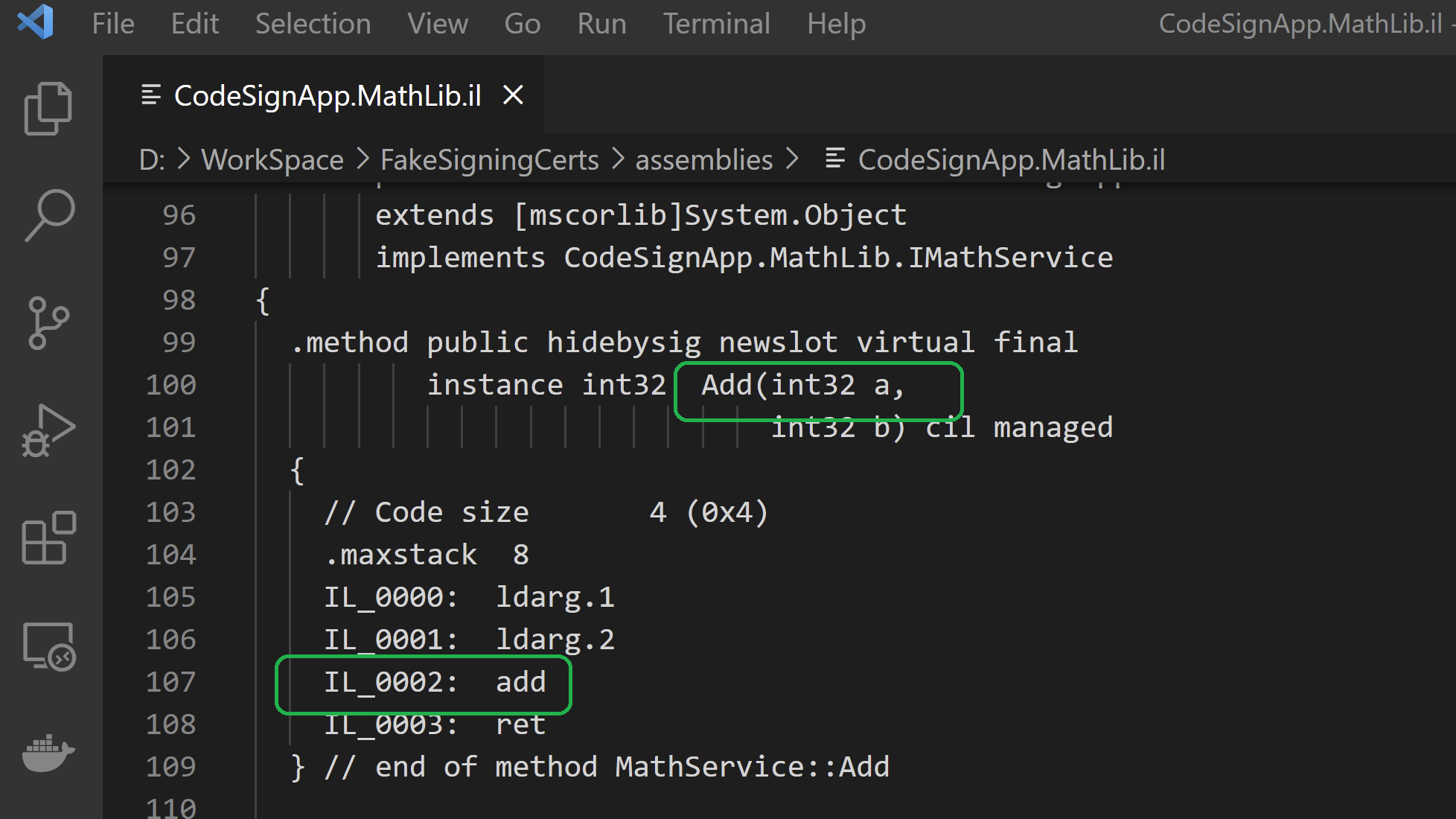
Edit the IL code
Export the public key from Strong name key so that we can supply the public to Visual Studio for Delay Signing the executables.
-
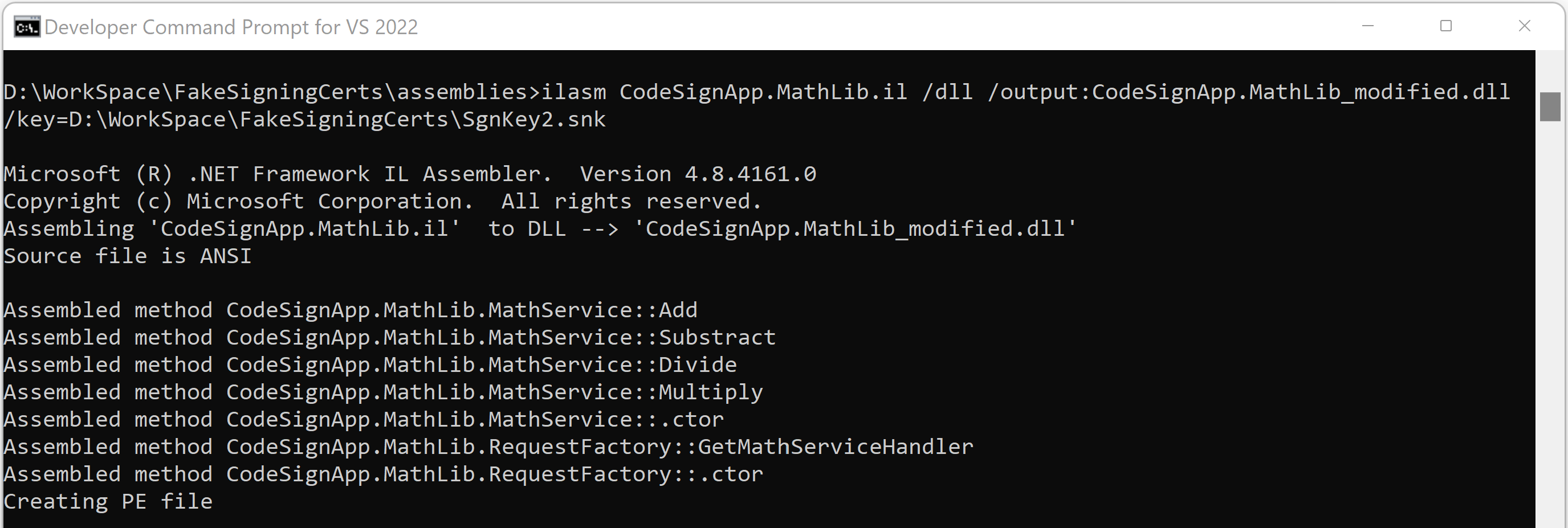
Reassemble the IL code back to DLL
Used VS Developer command prompt for running ILASM command. We are supplying the attacker's StrongName key to sign the modified DLL.
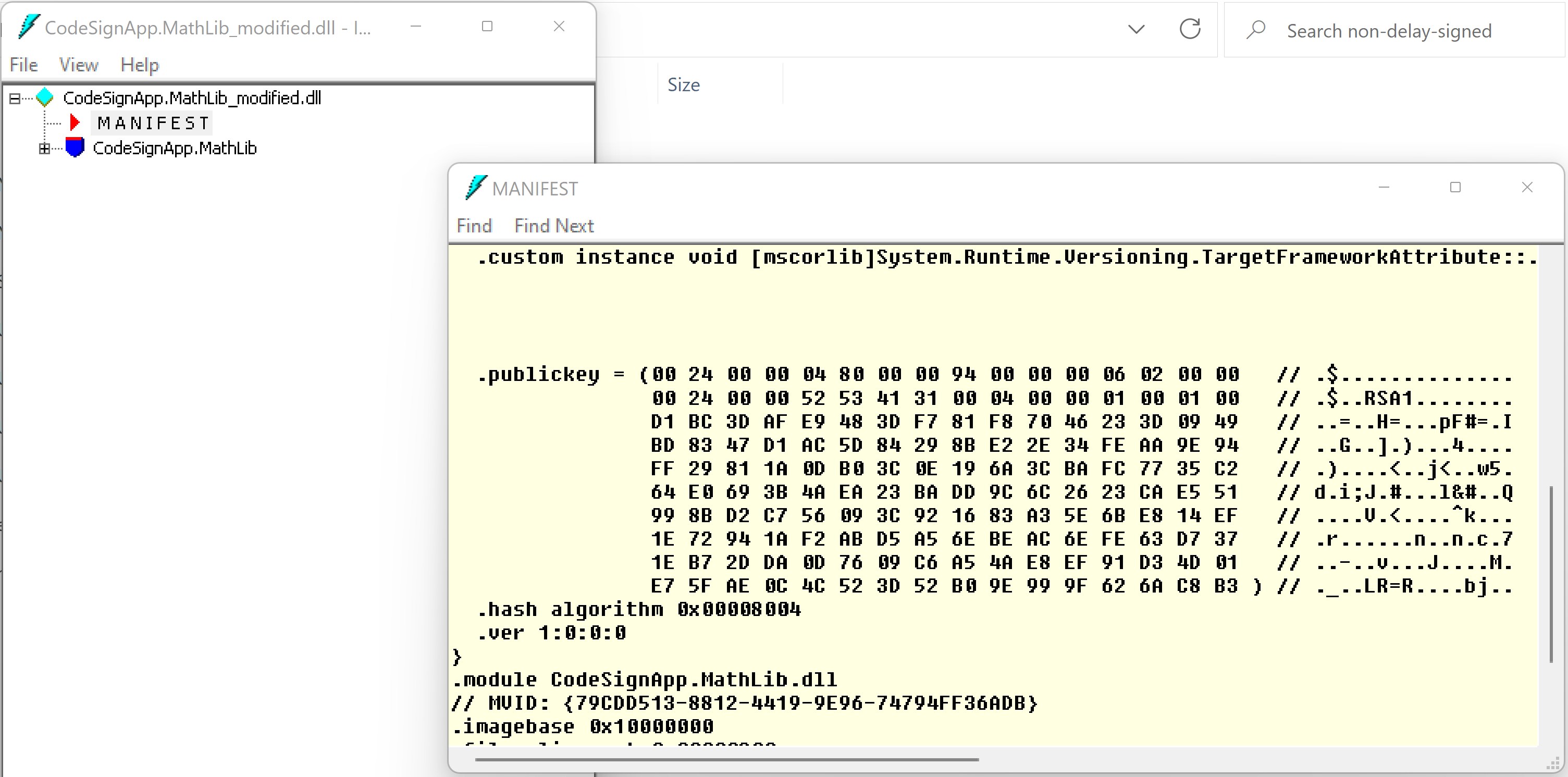
The StrongName public key has been replaced with the public key of new key(SgnKey2.snk) in the DLL manifest.
-
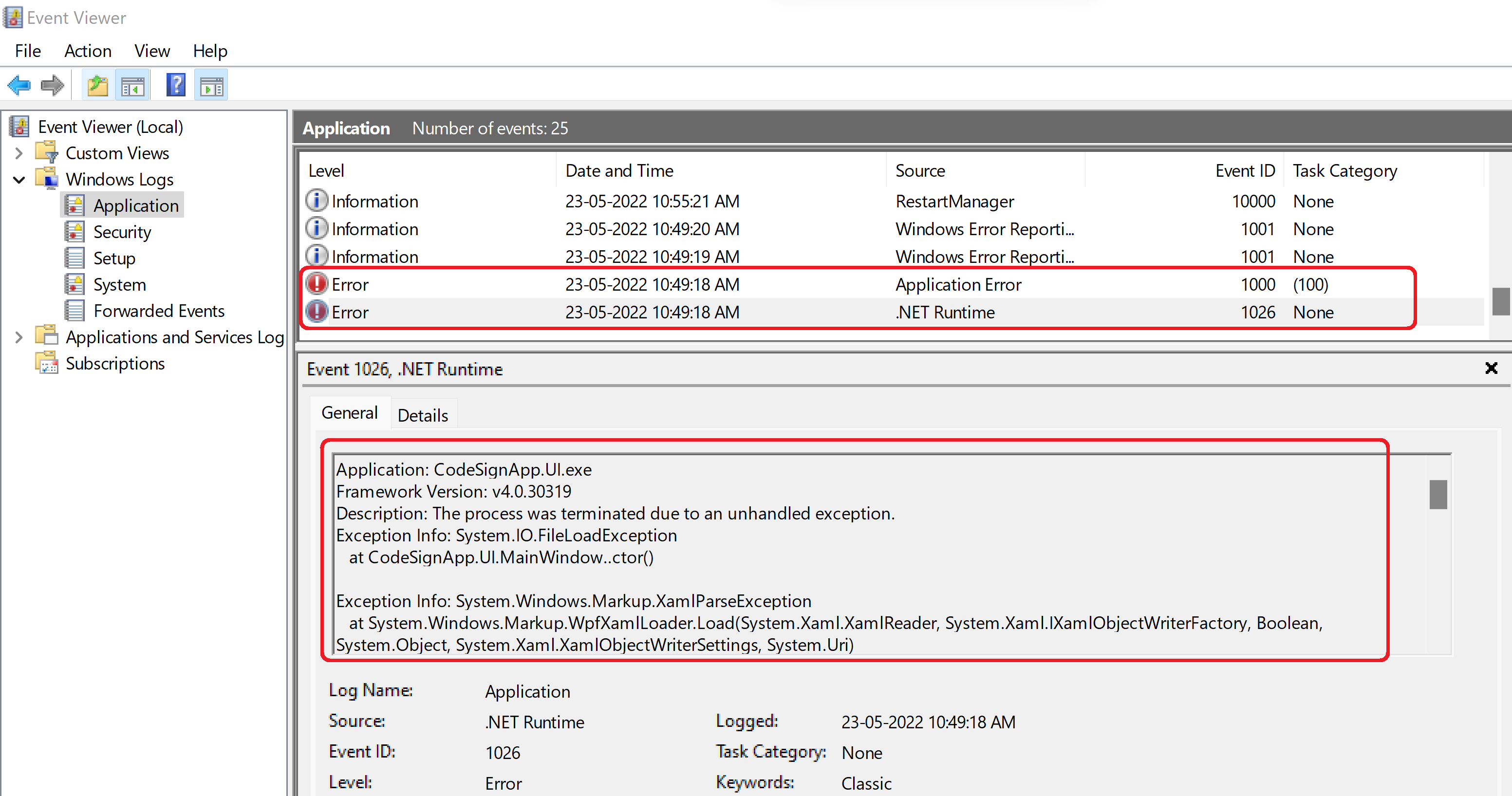
Application crashed!
Application didn't even bootup. We can see below error in Windows Event log. Event log error details was not very helpful to identify the issue.